The most cost-effective and absolutely reliable way to securely network all your sites over the Internet.
What We Do To Keep You Always Connected
Our Appliances Reliably & Securely Connect Remote Network Devices Together over Any Internet
The World’s Longest Ethernet Cable™
We provide secure connectivity to IoT/M2M & Hybrid Cloud Access & Connectivity Networks.
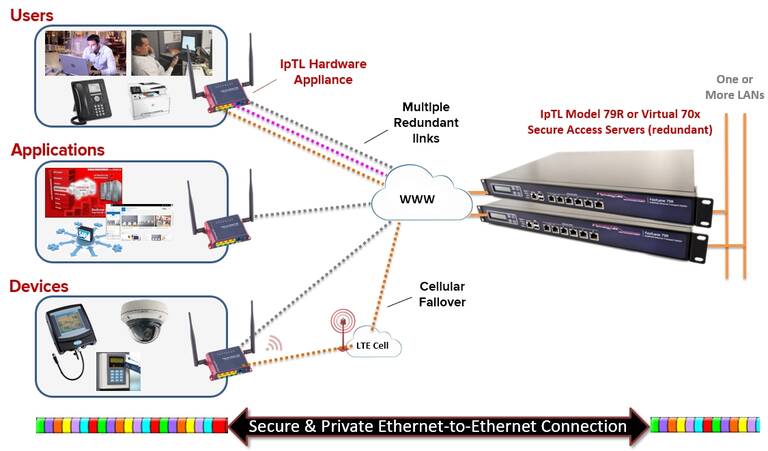
Our appliances connect your remote Ethernet devices to one or more central sites with reliability, security, and transparency. We make it easy to reliably get connectivity over any IP link.
- Allow you to connect your remote network devices together over any Internet link
- Provide an Ethernet Tunnel (L2 / Bridged) without any NAT, DHCP, or Routing issues
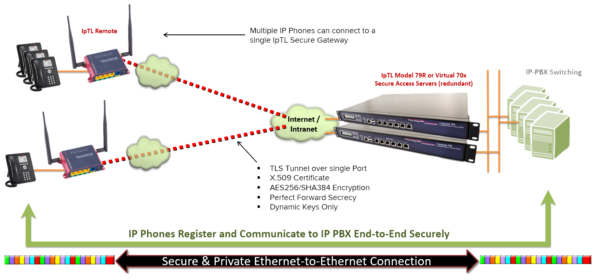
- Give you a true security end-to-end with dynamic keying, AES256/X.509 out of the box
| Dynamic-IP – on both ends of the link | Use any IP/Internet connection – xDSL, vSAT, Cellular, Cable |
| Connect any Ethernet device end-to-end | We work with IP, IPv4/6, and non-IP based devices without change |
| Totally transparent to the device data | We move Ethernet frames exactly like sitting on your LAN |
| True end-to-end security | AES256, X.509, Dynamic Keys – Preconfigured out of the box |
| Multipath tunnel bonding and dynamic switching | Dynamic Switching provides the best path at all times |
| Tunnel obfuscation & Data Whitening | Truly keep your underlying communications private |
Active/Active Full mesh with Active/Passive Cell Failover/Restore
Dynamic IP, NAT Friendly, & Bonded Tunnels
You can use any Internet to Connect All the Time
We don’t use the network address as part of the security association. Instead, IpTL secures the link with Dynamic-IP and NAT friendly technology which don’t cause hang-ups, drop-outs, and loss-of-fidelity.
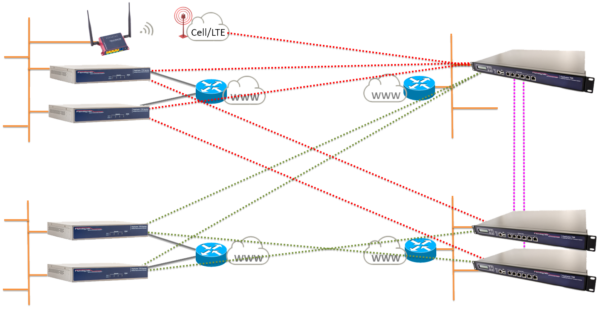
Our multipath tunnel bonding and our exclusive SystemMonitor™ enables you to aggregate and hot-switch between multiple the best path. You can also have simultaneous tunnel paths over a single provider link or aggregate multiple provider links to gain bandwidth and redundancy.
Dynamic Multipath Failover & Restore
Active/Active and Active/Passive Keeps You Up
We can eliminate any single point of failure in your communications chain. IpTL offers key technologies to protect your comms:
- Active/Passive – One or more connections with one tunnel and data path in use
- Hot-Active Multipath – Multiple tunnels with data path across one tunnel in use
- Active/Active – Multiple tunnels bonded together data across multiple tunnels
With these methods, you can provide up to 64 separate logical or physical failover connections. It is also possible to combine technologies. For example: you have multiple provider paths with independent bonded tunnels (active/active) and use cellular backup if the physical provider is down.

IpTL’s BlackNoise™ gives you Whitened Data
We keep your tunnel Unblocked, Unfiltered, & Private
You expect your links are private and it shouldn’t be obvious what your communications are. Traffic analysis and inference attacks can deduce information from your patterns and can be performed even when the traffic is encrypted.
IpTL’s BlackNoise™ set of obfuscation and path optimization techniques can remove tunnel, data, & traffic fingerprints and keep your links unblocked, secured, and private. It is trivial to filter our IPsec tunnels and may firewall and proxys are doing just this. Simpley, IPsec cannot give you privacy, security, or the ability to remain unblocked.
IpTL, with TLS and FastLink pipes, can keep your links up and private.