IP Camera CCTV Security & Privacy

How Do IpTL Secure Network Gateways Protect You?
The World’s Longest Ethernet Cable™
Network security is critical, and vulnerabilities are everywhere. With physical security devices, such as Network Cameras, at remote locations locking down those devices is paramount.
IpTL appliances give you Trust and Control™ and enable you to implement Zero Trust architectures to protect the network from the device and the device from the network.
We make it easy to microsegment your devices using our IPShare™ feature or provide clientless and non-spoofable multi-factor authentication for your IP network cameras with our SuperNAC™ features.
Unlike 802.1x, IPsec, or Client MDM solutions, we can lock down your device, prevent island hopping, and keep your privacy end-to-end.
Key points about IpTL for IP Camera Connections
- Full end-to-end Encryption with AES256
- X.509v3 certificates for attributable appliance identity
- Dynamic Keys renewed every 5 minutes automatically
- Man-in-the-Middle prevention with mutually authenticated certificates
- Not a P2P/Relay platform – all data is between your tunnels
- SuperNAC™ Clientless & Non-spoofable IP Camera 2FA
- Zero Trust Microsegmentation with IPShare™ Network Virtualization
- Works with any CCTV IP network camera vendor over Ethernet
Block IP Camera Snooping, Spoofing, & Backdoors
Zero Trust & Microsegmentation
Protect Your Network from IP Camera Backdoors & Network Spying
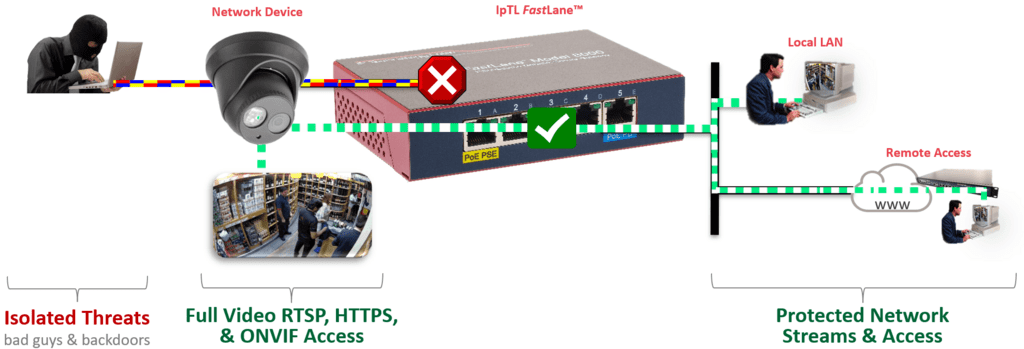
With IpTL appliances, you can easily lock down your IP network cameras, so only video (e.g., RTSP, HTTPS, ONVIF) passes through, and all other accesses are blocked. Our features enable Zero Trust and Microsegmentation architectures for total control.
Zero Trust and Microsegmentation are key tools to help you get control of your network devices. Zero Trust is the premise that all traffic and devices should be untrusted. Microsegmentation separates communications, so only expressly permitted traffic is allowed.
IP cameras and LAN devices do not need a “full view” of the LAN network and giving a device unfettered access is what hackers depend on. To stop them, you have to isolate and limit access.
First, by isolating your IP network camera, you instantly break direct LAN access. Thus, any vulnerabilities in the camera are simply blocked…including backdoors & scanning.
Second, only the desired data communications are permitted. For example, only video or ONVIF control will be allowed on the LAN and only to the requesting NVR or host. And with IpTL, that video will only be permitted when first requested from the LAN; otherwise, the camera is entirely cut-off. Once the request is no longer used, the camera access is shut off.
Your NVRs or monitors operate without any changes, and you are protected from snooping, spoofing, and bad guys.
How Does it Work
Network security is all about layers, and with IpTL, your network device does not have any access to the LAN or the Internet. The device will communicate with LAN hosts only after a connection request is first requested by a LAN host.
The isolated network device (e.g., IP Cam) is connected to an Ethernet interface (e.g., port 1) and supplied with a single private network address.
Further security can be added by locking the device’s unique MAC address to that IP.
The uplink port of the IpTL appliance is connected to the LAN and will act as the gateway firewall to the isolated device.
Connectivity from the IpTL appliance to the isolated device is strictly controlled. All accesses to the services of the isolated device are through the IpTL gateway firewall.
Instead of allowing all access, you can select only the services that are needed. Typical examples are RTSP, ONVIF, and HTTP.
IpTL includes a stateful unidirectional firewall that keeps the IP Cam isolated from the network until a LAN host requests a valid service.
Then communications will be permitted, only to that host, and only for that service for the duration on the connection.
This keeps the camera from scanning all IP addresses for hosts on your LAN or enabling any phone-home backdoors or island hopping off other devices.
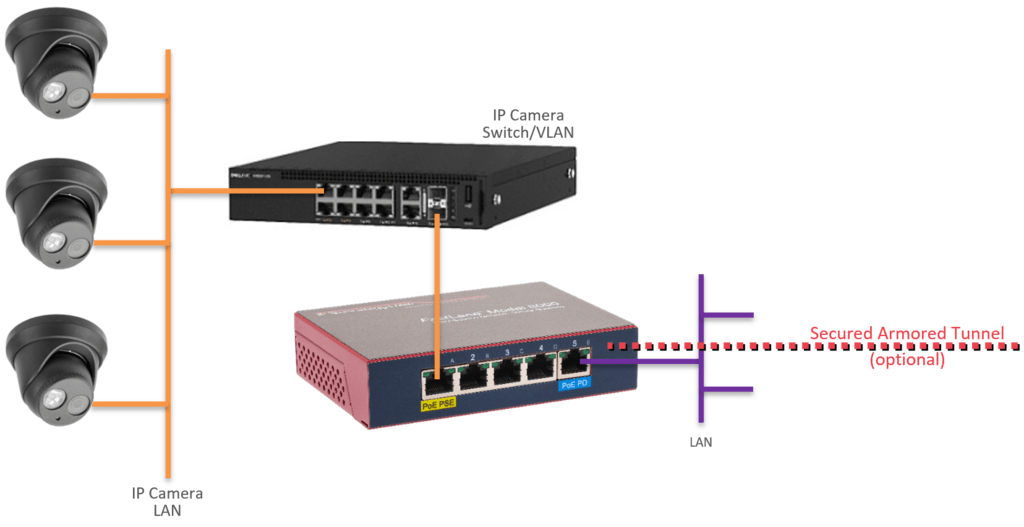
Protecting Multiple IP Cameras or IP Camera Network
Zero Trust and Microsegmentation are easy for multiple cameras. The IpTL appliance can be an intermediate gateway between the Network Camera/CCTV network and the production IT LAN.
It may be as easy as connecting the IpTL in-line from the security switch. For easier integration into existing networks, all IpTL appliances can terminate an unlimited number of VLANs.
Control Access to Internet Sites
Automatic URL Filtering to Stop Ransomeware & Controlled Internet Access
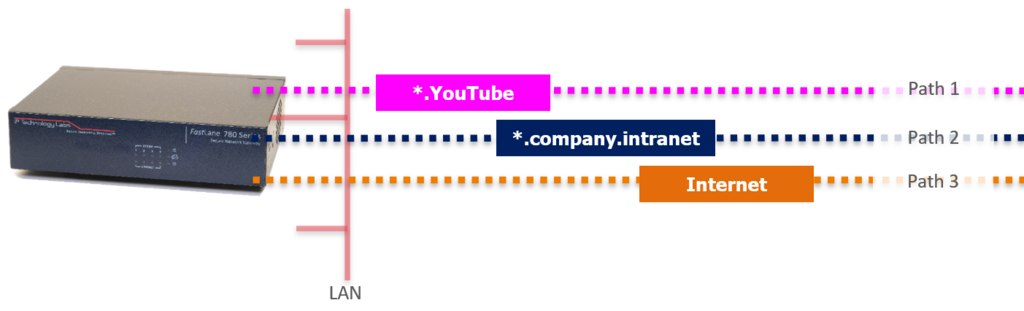
Sometimes you want your IP network Camera or CCTV service to connect to the Internet. This can be for cloud NVR Services or simply NTP time. Access Control Lists (ACLs) are a well-known way to provide access allow and block based on a known IP address. But Internet communications use URL-based names (e.g., www.iptechlabs.com), and trying to continually update your firewall lists just won’t work.
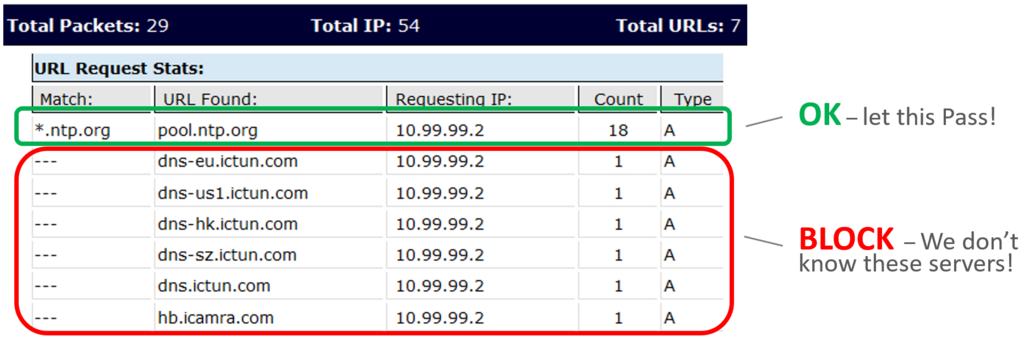
IpTL’s DNS SecureSwitch™ solves this by dynamically & automatically updating its ACLs based on the dynamically received IP addresses packed inside a standard DNS request. Now you do not have to manually update your ACLs based on IP but allow, block, or switch paths based on the URL.
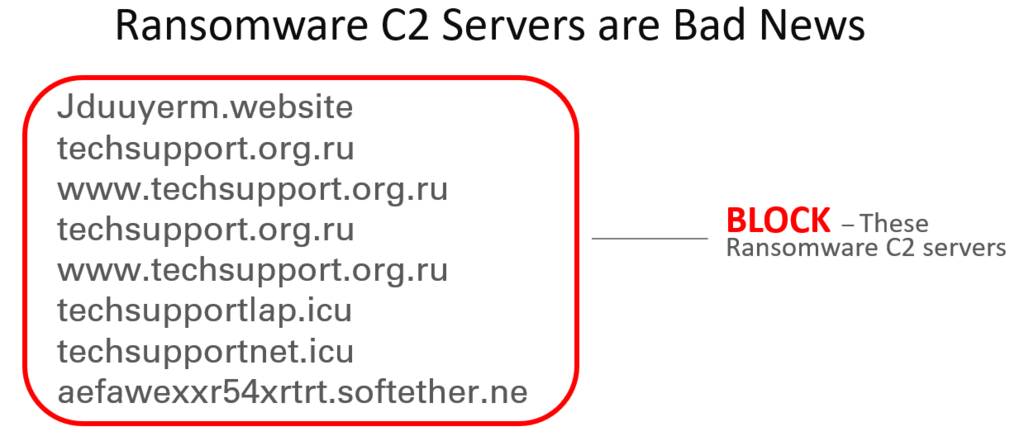
IpTL blocks Ransomware in two ways. First, Your devices never have visibility to your network, and you can stop active and passive scanning, services probing, and island-hopping in its tracks. Second, we block communications to command-and-control servers (C2).

How Does it Work to Protect Against Ransomware
With IpTL, you can protect the network from the device and the device from the network!
Stopping undesired communications, SecureSwitch™ enables dynamic allow rules for your trusted domains while blocking non-authorized names. Along with our dynamic connection-based firewall rules, only communications initiated from authorized hosts are permitted to flow.
IpTL blocks Ransomware in two ways. First, Your devices never have uncontrolled visibility to your network so that you can stop active and passive scanning, services probing, and island-hopping in its tracks. Second, we block communications to command-and-control servers (C2).
You want your device to do its job and nothing else…and we make that happen!
Device Identity & Access Control
Lockdown Network IP Cameras with non-Spoofable Identity Authentication
SuperNAC™ Agentless Device Identity features extend, protect, and automate the protection of local and remote control of IP Cameras, Access Control, and O/T devices.
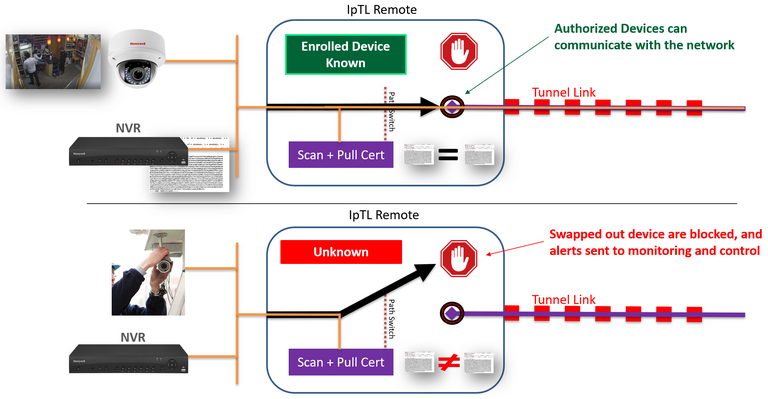
Going beyond looking at just packet headers or MAC addresses, SuperNAC™ provides positive assurance that the device you are talking to hasn’t been swapped out. Using active and passive profiling technologies, SuperNAC™ can model the posture of your network devices.
SuperNAC™ features run on your IpTL appliance and put you in control of your IoT device, not on some perimeter firewall.
Most NAC solutions expect you to install a client or run 802.1x. However, fixed application devices such as IP Network Cameras, and NVRs, Badge Readers are closed systems, and you cannot install a client. SuperNAC™ is agentless, runs on the local appliance, and means no installing, configuring, and paying for a per-host client.
IpTL’s patented TrustACL-CERT™ can verify a device’s X.509 cert and use built-in certificate extensions to control dynamic switching, ACLs, and segmentation for precision control on how and where communications can occur…directly attributable to your device.
How Does it Work to Protect Against Ransomware
How Does it Work
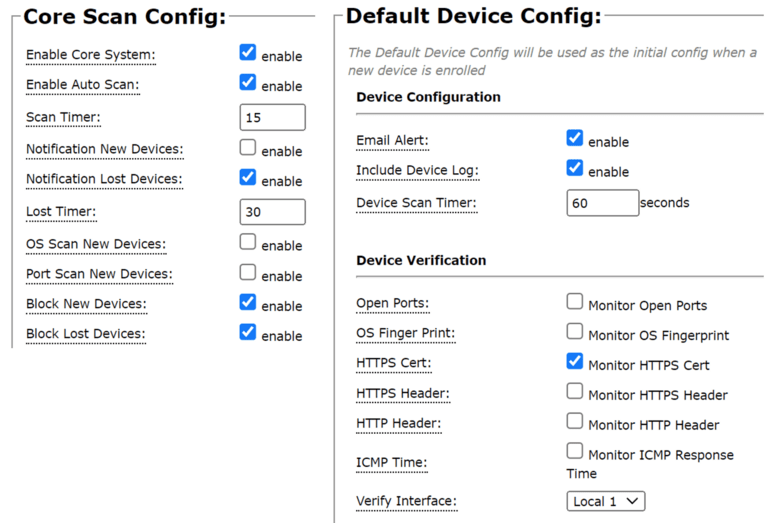
The SuperNAC™ feature is setup to pull the X.509 Certificate from your device, authenticate the response, and then update firewall rules to block or allow data.
SuperNAC™ is highly configurable and allows multiple-security scans to be all used together. Note: only the X.509 certificate method is unspoofable!
Through continuously scanning for devices and updating any connections, SuperNAC™ can automatically block and alert if an enrolled device has been tampered with.
This is all achieved without installing a client or agent on the device, and you can employ with any vendor or device that uses a web browser!
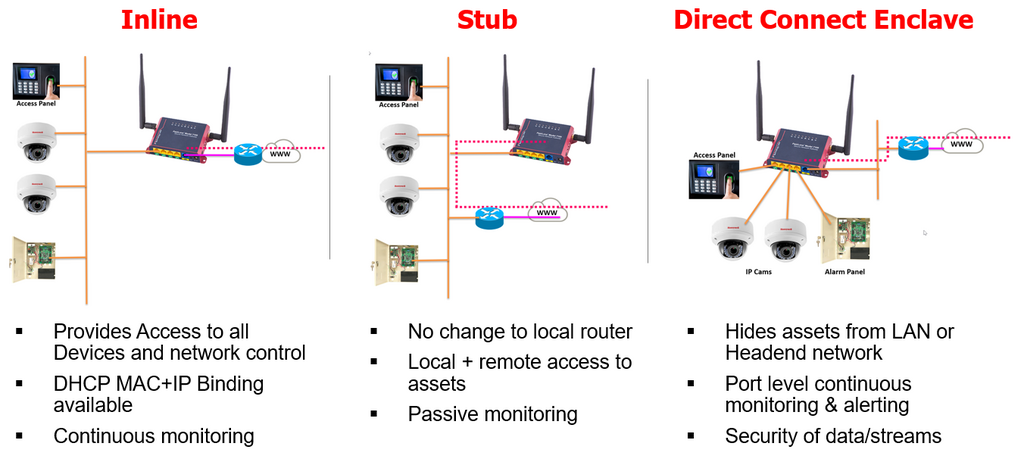
The End-Point is the Perimeter
IpTL appliances are flexible. Inline deployment provides base network access and protection. Stub allows local and remote access. Direct Connect Enclave gives individual port-based segmentation.
With SuperNAC™, you can deploy Connectivity, Trust, and Control in any network deployment.
See the Magic for Yourself with our Free Trial Demo
Sometimes you just need to see it for yourself. We’ve setup a program to do just that. Click the Try Now if you want to see the magic of IpTL absolutely reliable networking!