Protecting your Network from the Hacked & Hackable
Micro-segmentation at the End-Point: Device Enclave, Isolation, & Network Protection
Backdoors and bad guys go hand-in-hand. How do you isolate your device, like an IP Camera, from having access to your whole network? Using IpTL’s Secure Network Gateways, you can block known and unknown network traffic without limiting your access.
Challenges
Security alerts are going out every day about discovered backdoors in popular network-enabled devices. IP cameras, access control readers, and anything with a network port are vulnerable. The real threat is how do you protect the LAN from these devices? With IpTL’s Secure Network Gateways you can microsegment, enclave, and isolate those devices to ensure only desired network traffic is permitted. Here are some of the challenges.
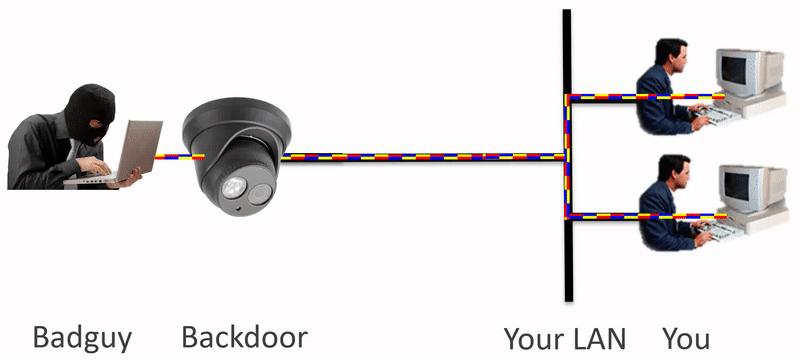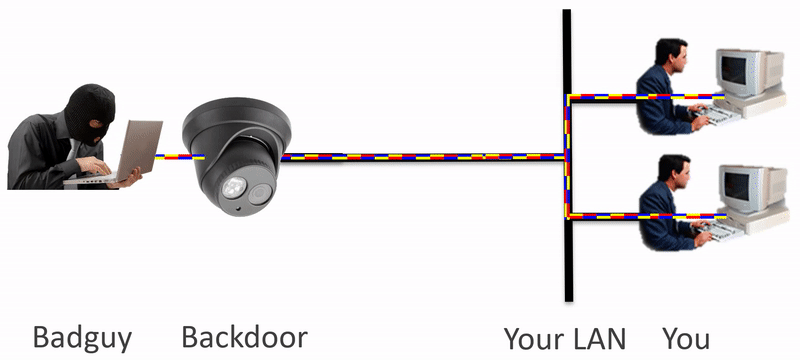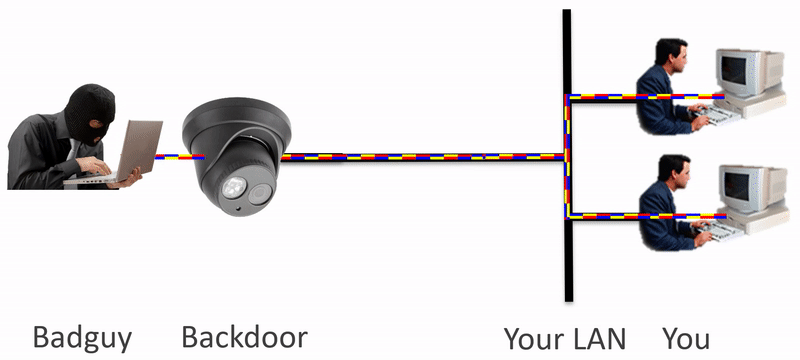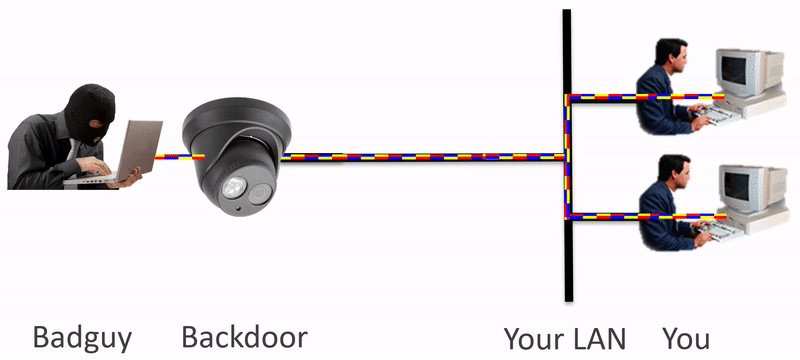
- Fixed Application Devices, like IP Cams, can have backdoors. Some allow the device to be tampered with while others enable access to your entire network and theft of your data
- You have to rely on the device manufacturer to provide firmware updates for known vulnerabilities, and they may not always acknowledge or fix the problem
- Unknown vulnerabilities still exist, and you are just waiting for the next zero-day.
- How do I keep unauthorized network traffic off my LAN?
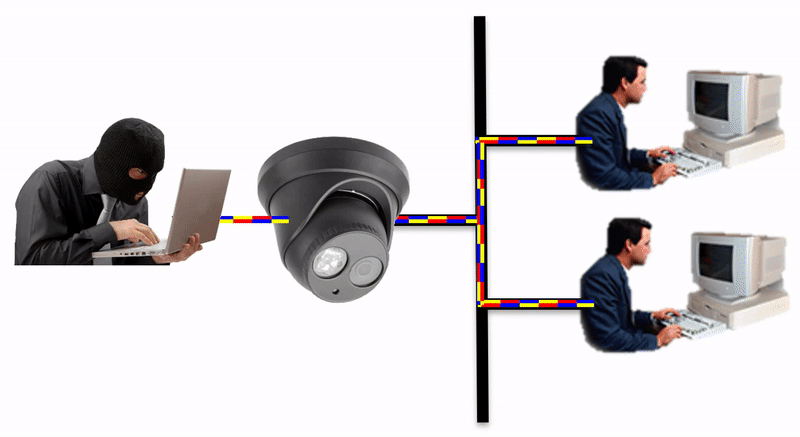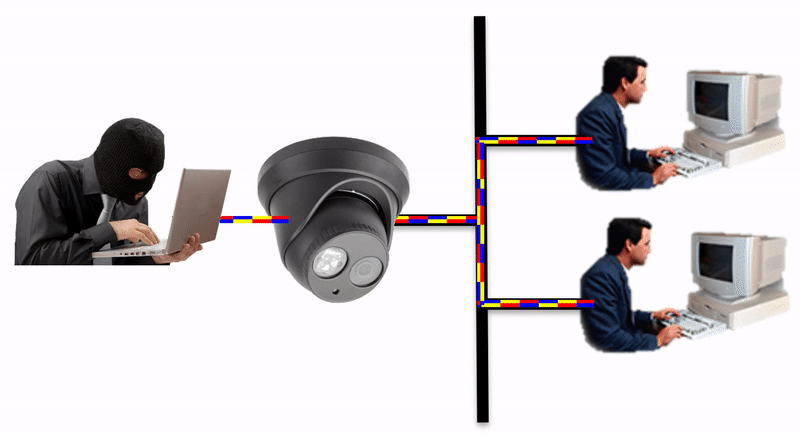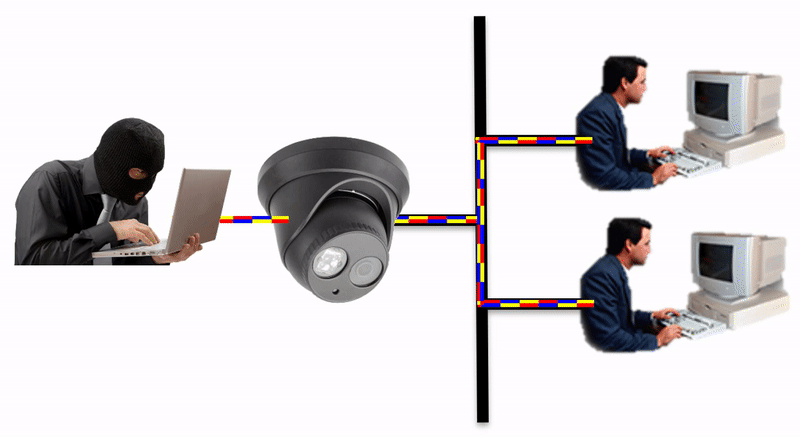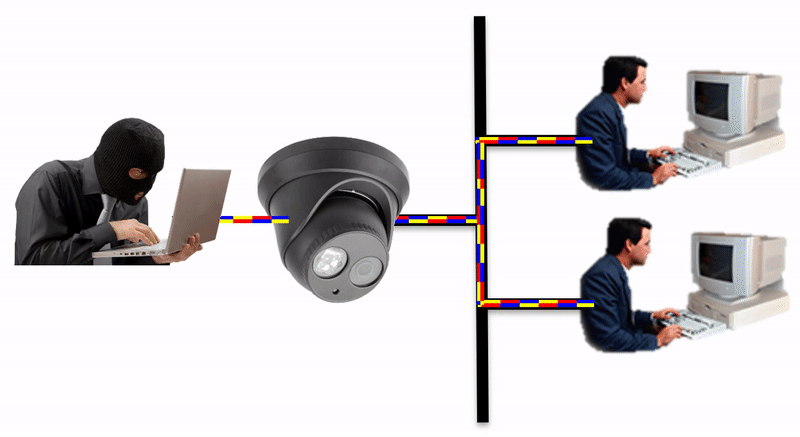
Isolate the IoT network device by placing an IpTL Secure Network Gateway in between the device and your network. This creates a logical and physical barrier between the networks.
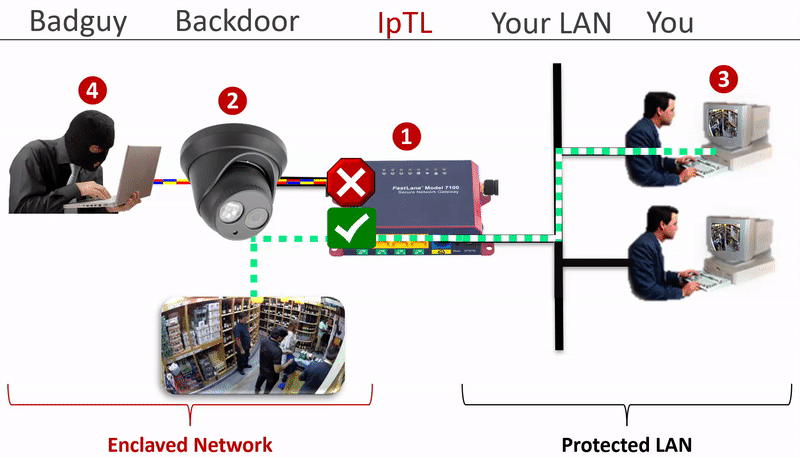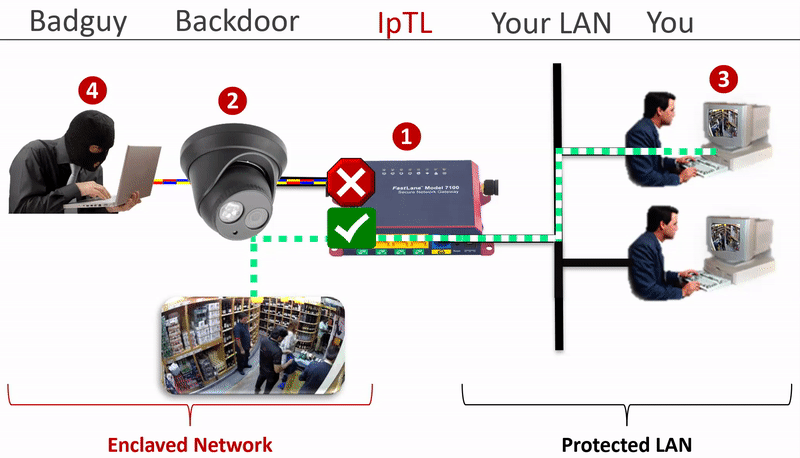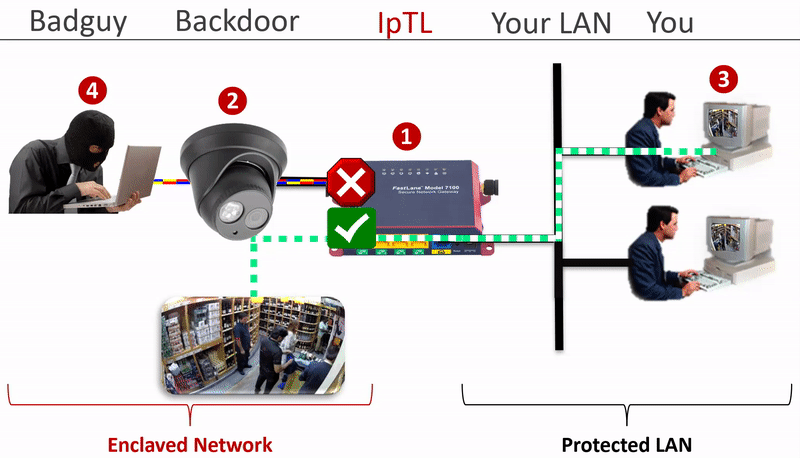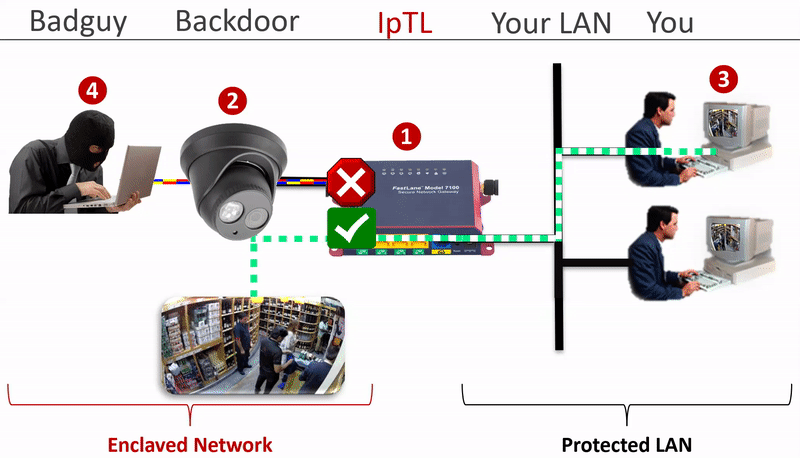
The IpTL Secure Network Gateway physically and logically separates the enclaved network from the LAN.
Additional security can be implemented by setting a SuperNAC™ application filter to only allows video camera data (e.g. RTSP or HTTP) to flow from the Enclaved Network to the Protected LAN. | |
| IP Camera is enclaved on its own network and the camera does not have direct access to the Protected LAN as the IpTL appliance is the gateway | |
| When the operator connects to the IP camera, SuperNAC™ creates a conditional pin-point connection between the camera and the operator only. Even when streaming the camera does not have access to the Protect LAN | |
| The badguy can’t “scan” the Protected LAN, even if he is using spoofing the IP camera MAC and IP addresses. Badguy cannot send malware into the Protected LAN as the network is blocked. |
Solution – How-it-Works
See the Magic for Yourself with our Free Trial Demo
Sometimes you just need to see it for yourself. We’ve setup a program to do just that. Click the Try Now if you want to see the magic of IpTL absolutely reliable networking!
Copyright 2019 IP Technology Labs, LLC. All trademarks are the property of their respective owners.