Access to Remote Devices Behind a Router/firewall & Protect with Conditional Access – All without changing the Network
Secure Remote Connectivity to Devices behind the Firewall
IpTL’s patent-pending IPShare™ gives you secure remote connections with conditional and deterministic access to network devices behind remote routers, firewalls, or NATs. IPShare™ can give you access even when you have no control over the remote customer site network, IP networking addressing, or access to the remote router.
As one of the SuperNAC™ suite of software-defined perimeter features, IPShare™ provides the following solutions to remote device access and security:
- Pin-point remote network access to devices like IP Cameras and NVRs
- Block all network traffic over the VPN except when requested by a host
- No need to configure the router or renumber the LAN – overlapping IP addresses are ok
Challenges
- You need access to a remote IP Camera or NVR but it is behind an existing router on a private network.
- Remote sites are NOT under the administrative control of the headend.
- You cannot “renumber” or modify the configuration of the network (e.g., port forwards, static IP, or have any network prerequisites).
- No access to the remote “router” to change settings.
- No ability to set “VLANs” or other 802.1x methods.
- Access may be wired Internet, but other sites will require Internet from LTE/Cellular; all are dynamic-IP and private IP.
- Need to prevent access into the Headend network from the remote network (PC’s, Wi-Fi, etc.)
- Need to prevent random access into the remote network from the Headend network.
- Needs to scale from one to hundreds or thousands of remote locations.
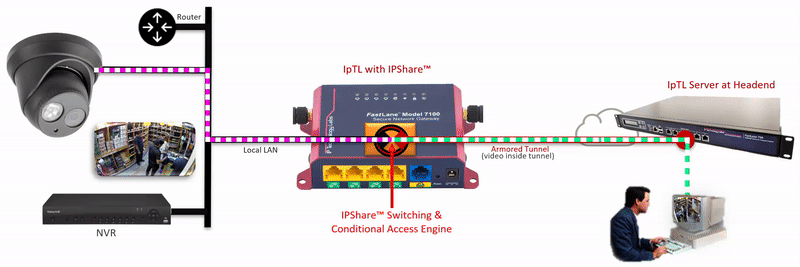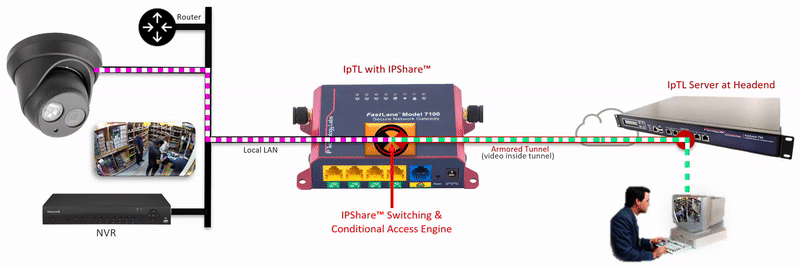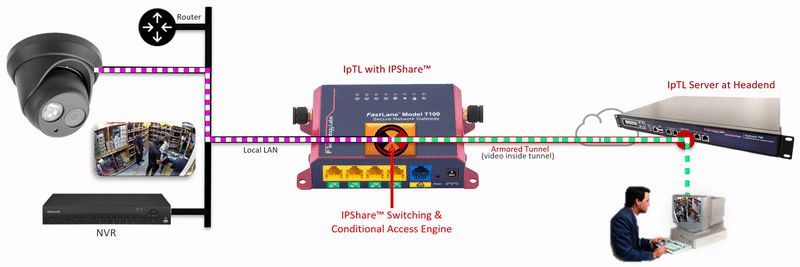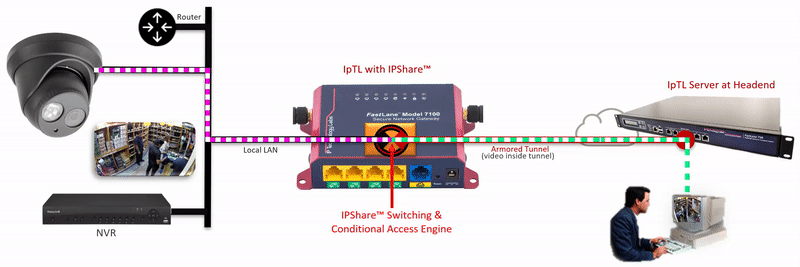
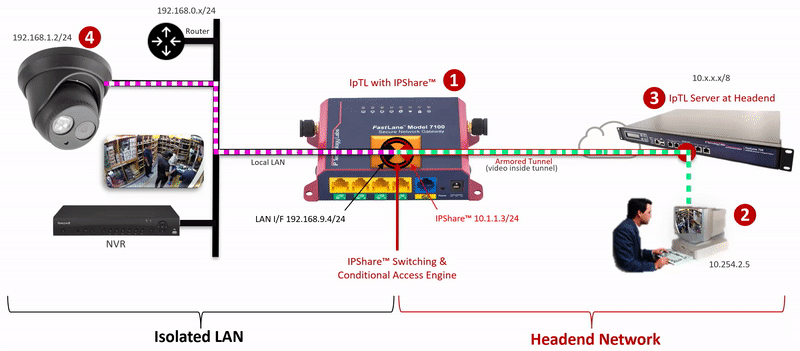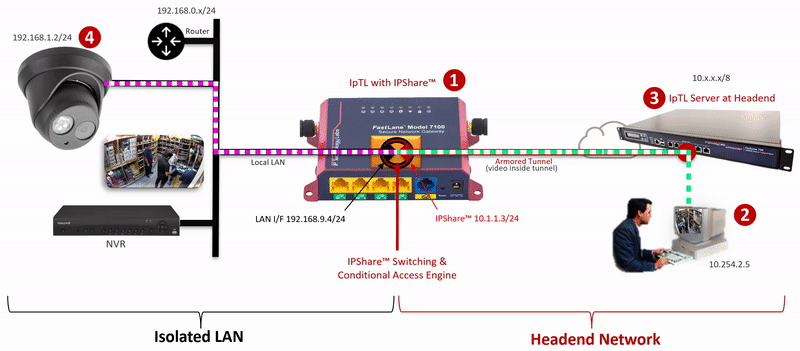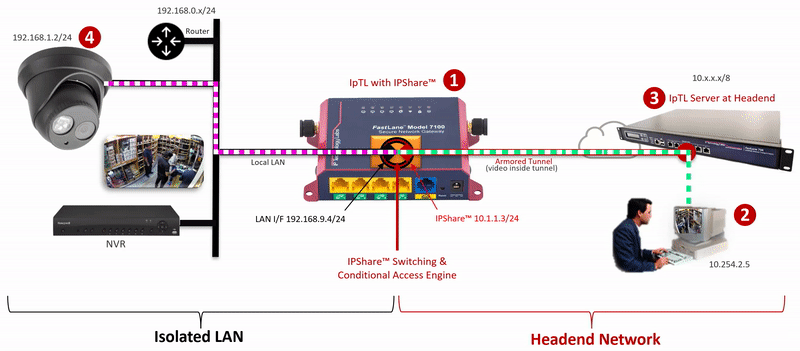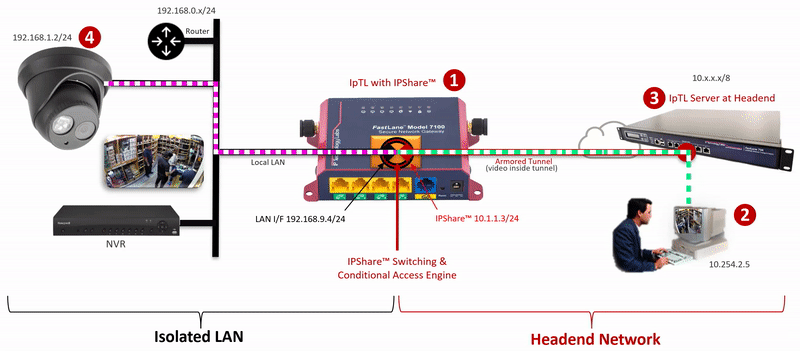
The IpTL Secure Network Gateway creates an Armored Tunnel to the Headend server over an existing Internet connection. On the remote IpTL appliance, the tunnel provides Ethernet LAN connectivity from the headend network to the IPShare™ switching engine. Locally, IPShare™ connects to the physical Ethernet LAN and then creates a routed interface, with NAT, between the Armored Tunnel and the local LAN.
On each side of the IPShare™ engine the network addressing space remains the same. Therefore no new routes or router configurations are required, and you can connect multiple sites that have the same IP network. For extra security, enabling the SuperNAC™ connection-based switching prevents any traffic from traversing back up into the Headend Network.
| |
The user initiates an HTTP, RTSP or similar network request to the IP Camera.
Additional security can be implemented by setting a SuperNAC™ application filter to only allows video camera data (e.g. RTSP or HTTP) to flow from the Enclaved Network to the Protected LAN. | |
| The Headend server forwards local LAN requests over the Armored Tunnel to the remote appliance. | |
| IPShare™ forwards the user |
Solution – How-it-Works
See the Magic for Yourself with our Free Trial Demo
Sometimes you just need to see it for yourself. We’ve setup a program to do just that. Click the Try Now if you want to see the magic of IpTL absolutely reliable networking!
Copyright 2019 IP Technology Labs, LLC. All trademarks are the property of their respective owners.