| Easy, Reliable, Low-Cost Remote Access and VPN for your devices, applications and sites | Eliminate cyber threats and protect your IIoT/OT/ICS, network devices, and your network from spoofing, snooping, and backdoors |
Why IpTL?
How do you get Easy, Reliable, & Low-Cost Remote Access VPN to your devices, applications, and sites? How do you protect your IoT/IIoT, OT, and network-enabled devices and your network from spoofing, snooping, and backdoors?
Only IpTL can deliver on the promise of:
- Easy and reliable end-to-end secure connectivity over any commodity Internet, without P2P or relay servers, and even when using Dynamic IP
- Endpoint device Network Access Control with microsegmentation and network virtualization providing non-spoofable multi-factor identity protection – all without installing a client or additional infrastracture
And all from a globally proven provider with incredible technical pre- and post-sale support.
Who we are?
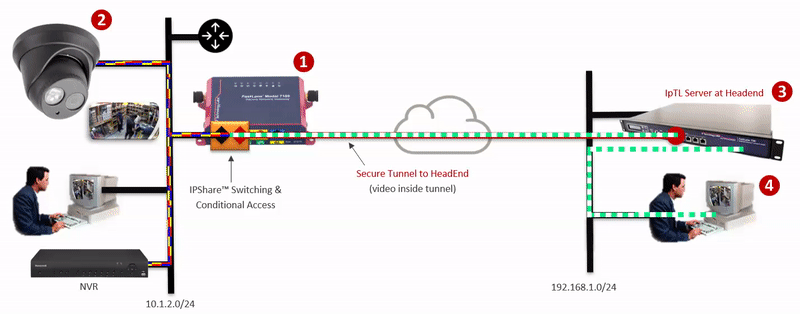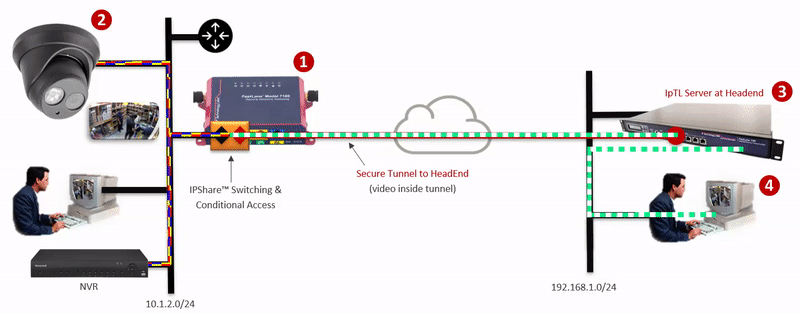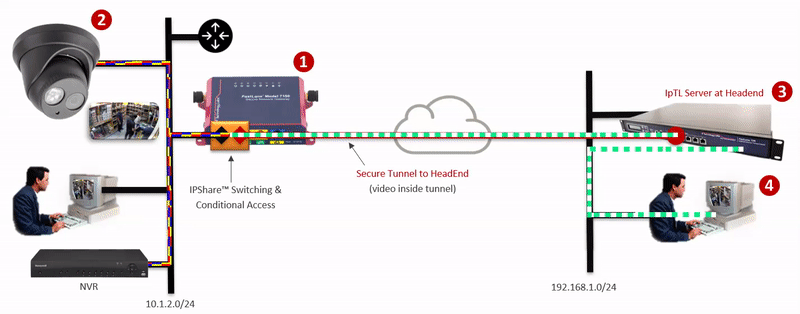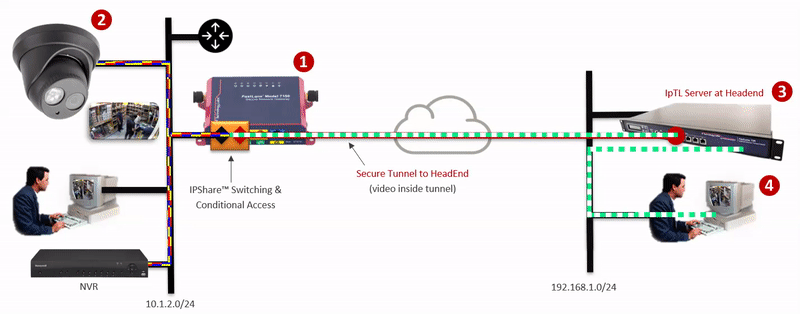
Founded in 2009 and headquartered in Baltimore, MD, USA, IpTL was the first to take the incomplete feature of VPN and the features of security and make it into a reliable secure Remote Access connectivity solution. Our patented technologies enable transparent, secure, and reliable end-to-end connectivity while supporting clientless micro-segmentation and zero-trust identity-based deployments.
Used in over 73 countries worldwide our customers come from all sectors including fintech, agriculture, energy, healthcare, security, telecom, and government. And their applications are diverse including VoIP LAN extension, Branch IP Camera Offload, Remote Oil Field Redundancy, ATM Cellular Failover, and Data Center Cloud-to-Cloud connectivity. Enabled by ease-of-use and automatic remote management, our solution is unmatched by any of the big-box vendors, carriers, or other do-it-yourself software technologies. Click here for more about us.

6 Reasons to Consider IpTL?
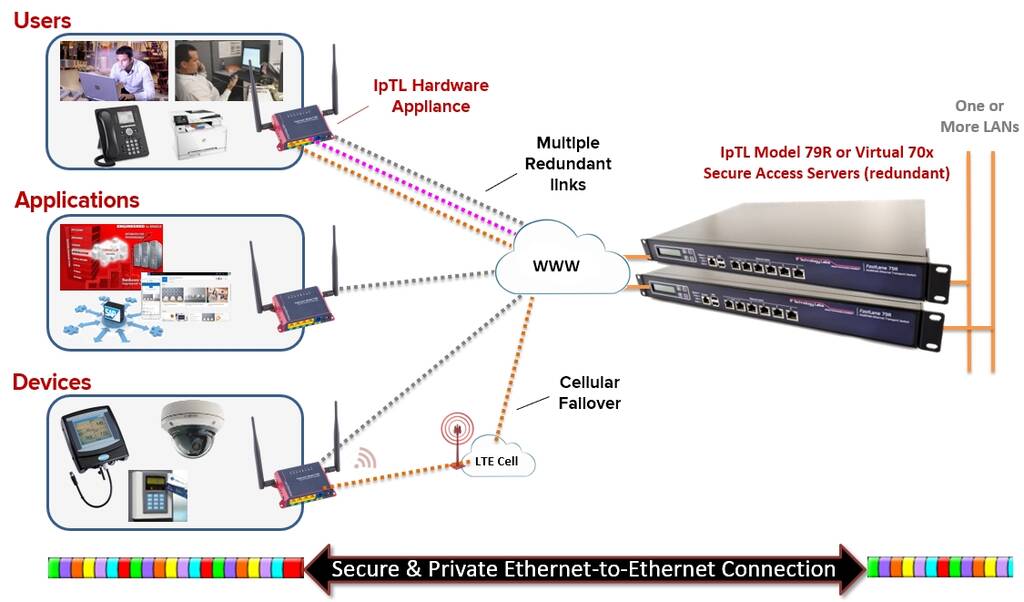
IpTL’s FastLane™ appliances offer the best Remote Access Tunneling & VPN along with Device-based security reliable and secure Ethernet and IP connectivity.
Whether you are connecting two-sites together for VoIP LAN extension, ATM machine MPLS leased-line replacement, or branch office connectivity with failover; IpTL can easily scale to your application and give you the network you want with the network you have.
There are six main reasons to consider IpTL FastLane™ secure gateways.
| Easiest Tunneling | Remote Access & VPN for IP Cams, Access Control, Ethernet OT for devices, applications & site-to-site applications in an already-figured-out-for-you configuration. Connect in minutes instead of wasting days troubleshooting. |
| Superior Connectivity | End-to-End transparent networking even with Dynamic-IP and supporting VLANs, Multicast, and Overlapping IP addressing. Robust access router gives you all the tools to seamlessly integrate into your network. |
| Highest Availability | Built-in Redundancy & Resilience with the Fastest failover/restore with tunable failover parameters available today. Use with multiple ISP’s or fail to Cellular/LTE without disrupting your networking. |
| Best Management | Full-touch out-of-band direct access and control of all your endpoints and built-in dynamic IP resolution. Control your appliances anywhere in the world even if they aren’t connected to your headend. |
| Highest Security | Integrated Network Access Control (NAC), multifactor authentication (2FA), & Network Virtualization, and SPI/ACL Firewall – all without Clients or reconfiguring your devices. |
| Best Privacy | AES256 Encryption standard, X.509v3 Certificate-based dynamic keying, without any P2P or Relay servers; fully encrypted End-to-End between your devices only. Only IpTL can deliver a full-up solution that doesn’t touch any 3rd-party server – including ours! |
Easiest Tunneling
- Our VPN is all-figured-out-for-you. We make it easy to setup a tunnel/vpn by pre-configuring all the X.509 certificates, use dynamic keying that regenerates automatically every 5 minutes, and align the security association so it works right. We use TLS1.2, instead of troublesome and complicated IPsec, and give you the proven tools to lock down even further. Use our AutoConnect™ feature for true Plug-and-Play connectivity; even behind a router, firewall, or NAT.
- Less than 5 min to Setup and Connect. You only need to configure the remote peer to establish a fully secure link, so there is no need to pay for extra engineering time with difficult and lengthy setups, which may not work, and delaying final handoff to your customer.
- Works on Dynamic IP connections, through NAT routers, and Nested NAT Internet services. Unlike IPsec, IpTL FastLane™ does not use the IP address as part of the security, can work with a private network address and a static or dynamic public IP, and is NAT friendly. So you can make a link where others fail, can use low-cost Internet connections, your tunnels are not blocked from NAT routers and all your applications work unrestricted.
- Use on ANY IP network including private leased lines, satellite connections, and cellular datalinks. Of course, standard xDSL, Fiber, and cable modems work great too as well as LAN point-to-point applications. Give us an IP connection and we’ll make it work.
- AutoConnect™ and Tunnel Compression. Patented AutoConnect™ allows a point-to-point tunnel without configuring a port forward on your router. Tunnel compression enables more throughput often gaining any losses due to tunnel headers. You can have an Immediate link without tracking down, and fighting with, the person who knows how to configure the gateway.
Superior Connectivity
Our goal is to be transparent to your data and integrate into your existing networks. If you can put your data into an Ethernet frame we can move it across any network. Supports IP/Ethernet, multicast, IPv4/IPv6, as well as non-IP protocols…all at the same time.
- Tunnels Work in Blocked or Filtered Networks. IpTL FastLane™ appliances include technologies that allow the tunnel, keying, and management to use a single user-defined port or automatic floating ports. It also has options to remove any tunnel “fingerprints” to prevent blocks based on traffic by upstream inspection devices. Your connections and links and stay up reliably and your users and application can work without downtime or constant restarting.
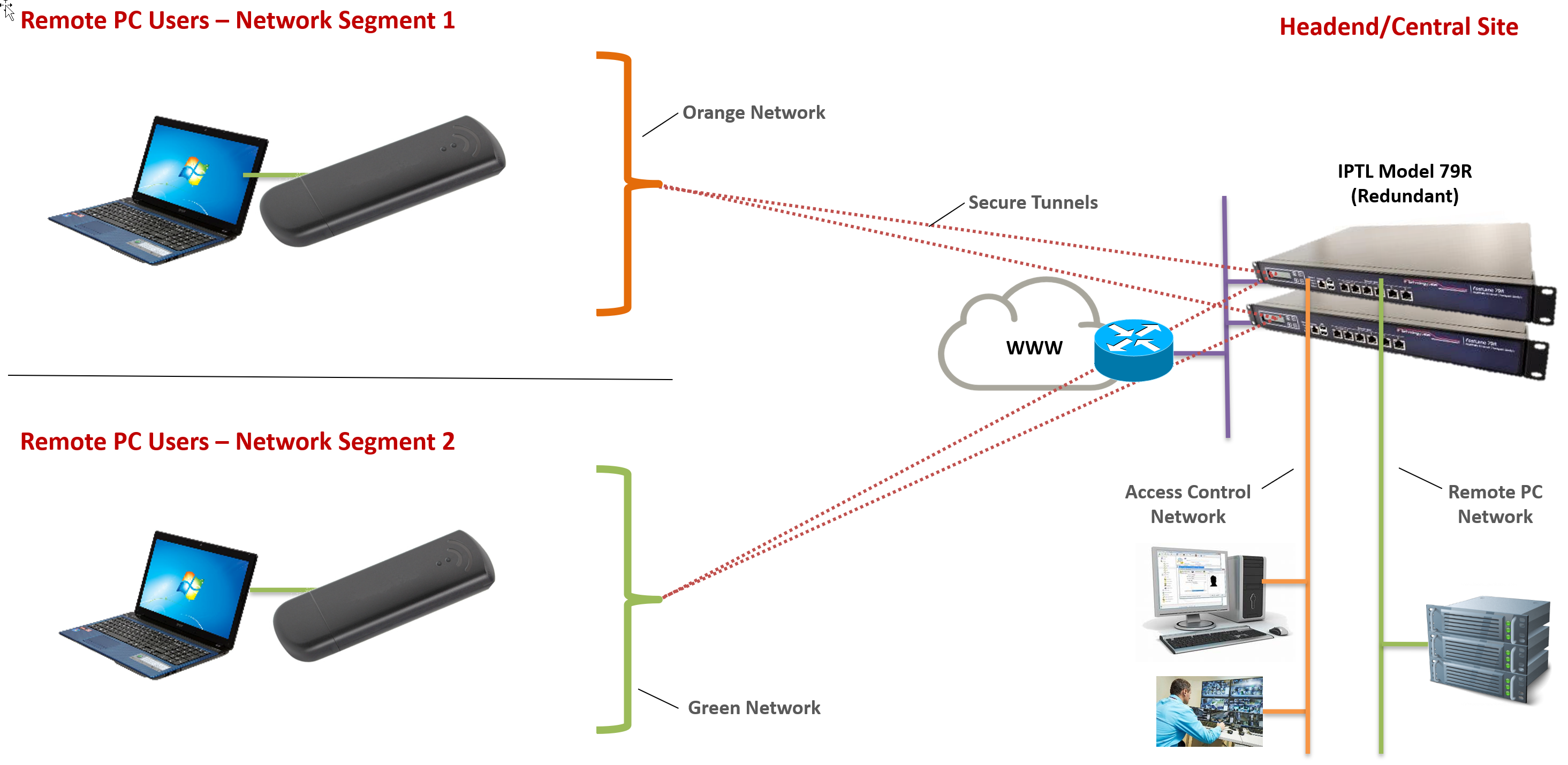
- Single platform for Site-to-Site and Remote Access. All IpTL appliances are based on the same software codebase, with all features compatible across all products regardless of your application or which IpTL appliances you use. You can recommend and deploy any IpTL product and not lose money, time, or credibility due to incompatibilities.
- Robust Access Router and Firewall and data control. We provide all the standard tools and configuration options to ensure seamless integration into your existing network. Including DHCP server and client, unlimited secondary addressing, unlimited Port and Trunk VLANs, PPPoe, QoS, Full route table configuration, and SPI firewall for Layer2, Layer3 all the way to Layer7.
- DNSMonitor™ site control allows traffic control and site-based access control with dynamic creation of filter rules or automatic and dynamic route entries based on DNS query responses gives the control to ensure access to a site, or sites, goes down the path you want.
- IPShare™ Network Virtualization and Micro-segmentation. Provides access for overlapping addresses without network renumbering or static addressing appliances or hosts. You can connect and aggregate any network without address conflicts or assigning IP addresses to remote hosts.
Highest-Availability
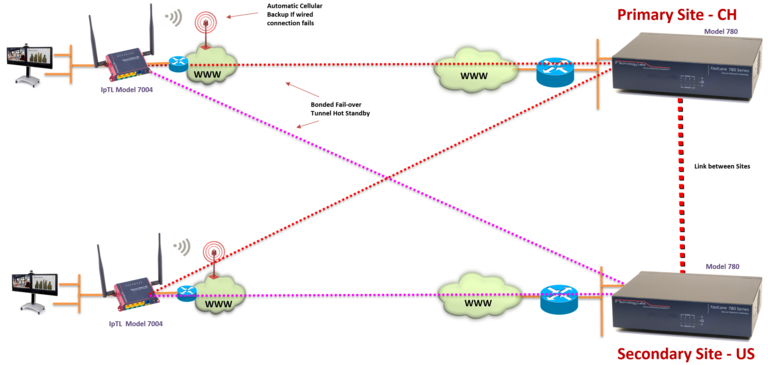
Only IpTL can ensure the world’s best network availability in case of a network device or path failure at any point in your link. Our SystemMonitor™ feature provides tunable failover/restore features unmatched in the market today. Our redundancy allows you to eliminate any single-point-of-failure across your networking including physical device protection as well as link protection. Use multiple ISPs, Wi-Fi, Cellular or all of the above.
- Active/Active Multipath Redundancy. Unlike other vendors that use Active/Passive (requiring clustering), IpTL maintains automatic and self-healing connections even if one your links or devices has crashed–you always know that the backup path is live and ready for action (reducing the 2 am call).
- WAN Link Auto failover with Multiple Internet Providers. Allows the use of multiple Internet connections to provide redundancy. IpTL FastLane™ appliances are not “physical port-based” and each device can natively support redundancy using up to 64 different Internet providers to different physical locations.
- Active Deadpeer detection with Multisite uptime failover mechanism. Other products wait for a time-out or require an admin to re-set the connection. IpTL FastLane™ can reliably and quickly sense a network fault and automatically redirect the network connection to remain live without having to intervene.
- No MAC Spoofing VRRP / HSRP complications. There are no fake network interfaces or clusters of “standby” equipment for redundancy. You have a more reliable network, can avoid complicated setups, and eliminate instability during a network disruption. Of course, we do offer VRRP as a feature should you require it.
- Multi-interface Tunnel Link Bonding & Load balancing. Aggregates bandwidth and tunnels with up to 64 different Internet provider links. Not only will you have faster and reliable connections without wasting resources on dormant services, but you can aggregate enough bandwidth for sites that were previously underserved by existing networks.
Best Management
Only IpTL provides a single interface and one-click setup, with role-based credentials to manage your appliance anywhere world-wide—even if installed behind another network.
- Full Touch Out-of-Band Management & Centralized Management System. Provides access to setup, monitor, configure, and manage your appliance regardless of where it is in the world–even when it is not tunneled to your server. We’ve architected our solution so it can run 100% on your network giving you the highest levels of security and control.
- Management through NAT/Nested NAT. You aren’t blocked from access to your remote devices even if they are installed behind someone else’s network. No more waiting to “bring it in” for support.
- One click setup. Set the server MAC address on the remote appliance to immediately achieve a fully secure transparent tunnel between networks–unlike other vendors that require complicated and insecure configurations that can require hours to get up and running.
- Granular Role-Based Management Credentials. Set different username/passwords for individuals who monitor, configure, and control the appliance—allowing you to eliminate “standard” or “default” users like root, sysop, and admin default passwords, which increases security and regulation compliance which require these be disabled.
- Single management interface across all IpTL products. A single, consistent and intuitive interface across all IpTL products and applications, using industry common terms, makes it easy for your team when setting-up or maintaining your remote access system.
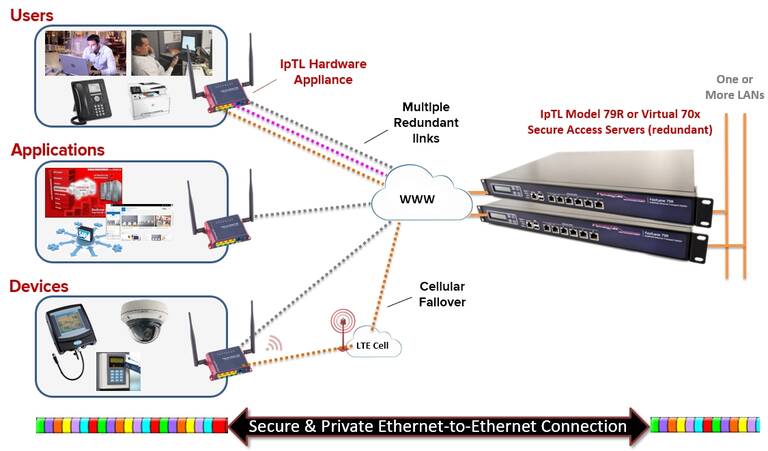
Highest-Security
- TLSv1.2 Tunnel. Provides the highest level of industry security (more secure than SSL) protecting against the latest attacks while supporting much higher privacy and encryption than out-of-the-box IPsec. With built-in X.509v3 certificates in each appliance, each link is provided with positive identity and source key material.
- AES 256 GCM/SHA3 & Perfect Forward Secrecy. Provides BOTH of the industry’s leading encryption strength and privacy standards—set by default. Assures your personal and corporate data remains private and protected so you don’t have leaked information that can lead to civil, financial, and legal liability.
- Configurable Dynamic Re-key/No PreShared Key. Most companies use a pre-shared key because it is easy to configure–but it is insecure and can be hacked because it is seldom changed. IpTL FastLane uses a dynamic key that is automatically generated per session and re-generated based on time or traffic volume—providing unequaled security without any manual configuration.
- Device usernames and tunnel passphrase. Only remote appliances are authorized to connect to your network. Tunnel passphrase creates a closed-user-group and prevents any non-authorized IpTL appliances from connecting to your network and keeps your server hidden from hackers doing port-scanning and denial-of-service attempts.
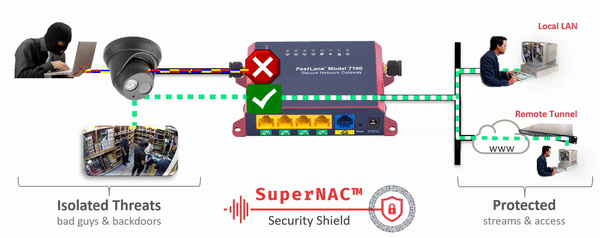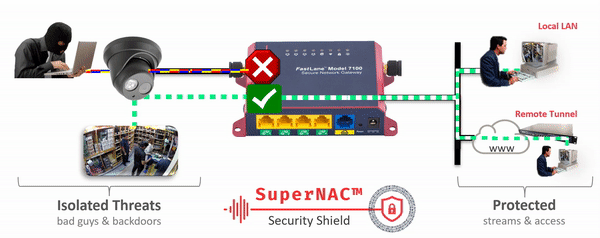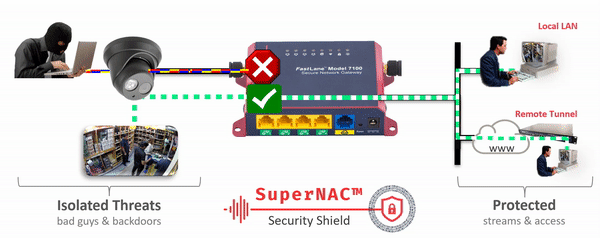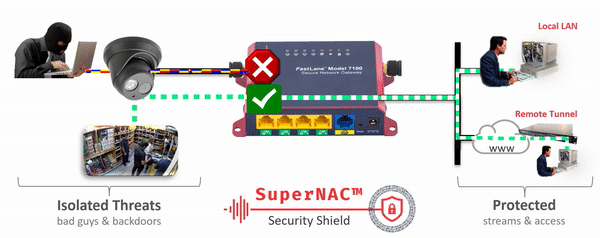
- Device and Network Virtualization. Now you can Deploy Zero Trust architectures with microsegmentation and network virtualization easily and cost-effectively. Our patent-pending IPshare™ gives you the ability to regain Trust and Control™ over every network-enabled device.
- Clientless identity and Network Access Control. with IpTL’s patent-pending SuperNAC™ feature set, we can lock-down your network devices and only allow access to those authorized. Other vendors can only do this “if you install their client” or they suggest passive schemes that can be easily spoofed. Only IpTL can provide you device-based chain-of-custody end-to-end.
- 100% Clean PCI DSS 4.0 Compliance and Scan. IpTL Fastlane is the only VPN/Tunneling appliance that has passed an independent 3rd party test lab scan with NO PCI DSS 4.0 vulnerabilities and without exceptions or violations. This helps enable merchants handling credit-card payments to have a clean audit and protect their reputation. Click here to request your copy of the test report.
Best Privacy
- OS Independent. Unlike other popular systems that require a device driver and client on the PC to work (and can break if you switch or update your OS (Windows 8 to 10, IoS, Android, etc.), All FastLane™ appliances are clientless and do not require any software to be installed or maintaied –if it can connect to Ethernet via wired or wireless it just works!
- Security End-to-End and Multifactor Authentication. Your data is protected and your security cannot be bypassed complete man-in-the-middle protection.
- Device usernames and tunnel passphrase. Only remote appliances are authorized to connect to your network. Tunnel passphrase creates a closed-user-group and prevents any non-authorized IpTL appliances from connecting to your network and keeps your server hidden from hackers doing port-scanning and denial-of-service attempts
- Obfuscation provides data whitening and removes data path fingerprints, as well as packet grooming and sizing eliminates traffic analysis on your data flows…including VoIP and Video.