The First Defense-in-Depth Point Source Cyber Resilient Appliance for Headless Devices
Seamlessly add true cyber end-point security to your network-based devices, ensuring no backdoors, alteration, or insecure communications. With an integrated hardware secure element using TPM2.0, the Model 8K provides secure boot, secure credentials, and a true random number generator for resilient device cyber security. With built-in 802.1at PoE+ PD and 802.1at PSE, you can power the Model 8000 and your PoE device simultaneously without injectors. The Model 8000 runs the complete IpTL firmware set with Armored Tunneling and BlackNoise™ obfuscation, SystemMonitor™ failover, DNS SecureSwitch™, and SuperNAC™ for a secure and attributable communications solution.
 When to Use
When to Use
- Branch office, Point-of-Sale, and ERP systems
- IP Camera Remote Access & Lock-down from Backdoors
- Microsegmentation and Zero Trust deployments
- Device Identity and Attribution with Non-spoofing Network Access Control & device 2FA
- Multi-point aggregation for up to 10 remote connections
- High-Performance network tunnel links for PtP, PtMP, or Cloud
Ideal Applications
- Ransomware C2 IoT device protection including SCADA, PLCs, and Controllers
- Higher bandwidth IoT & M2M Connectivity & Cloud Trunking
- Link Micro-segmentation and Tunnel trunking
- IP Camera Remote Access VPN
- IP Camera Protection & Identity
- NVR backhaul & Secure WAN offload
- Mid-large Branch data replication cloud connectivity
- MPLS or Lease-line redundancy over with Active/Active redundancy keeping your links up and running
- WAN Failover & Restore Access Link Protection
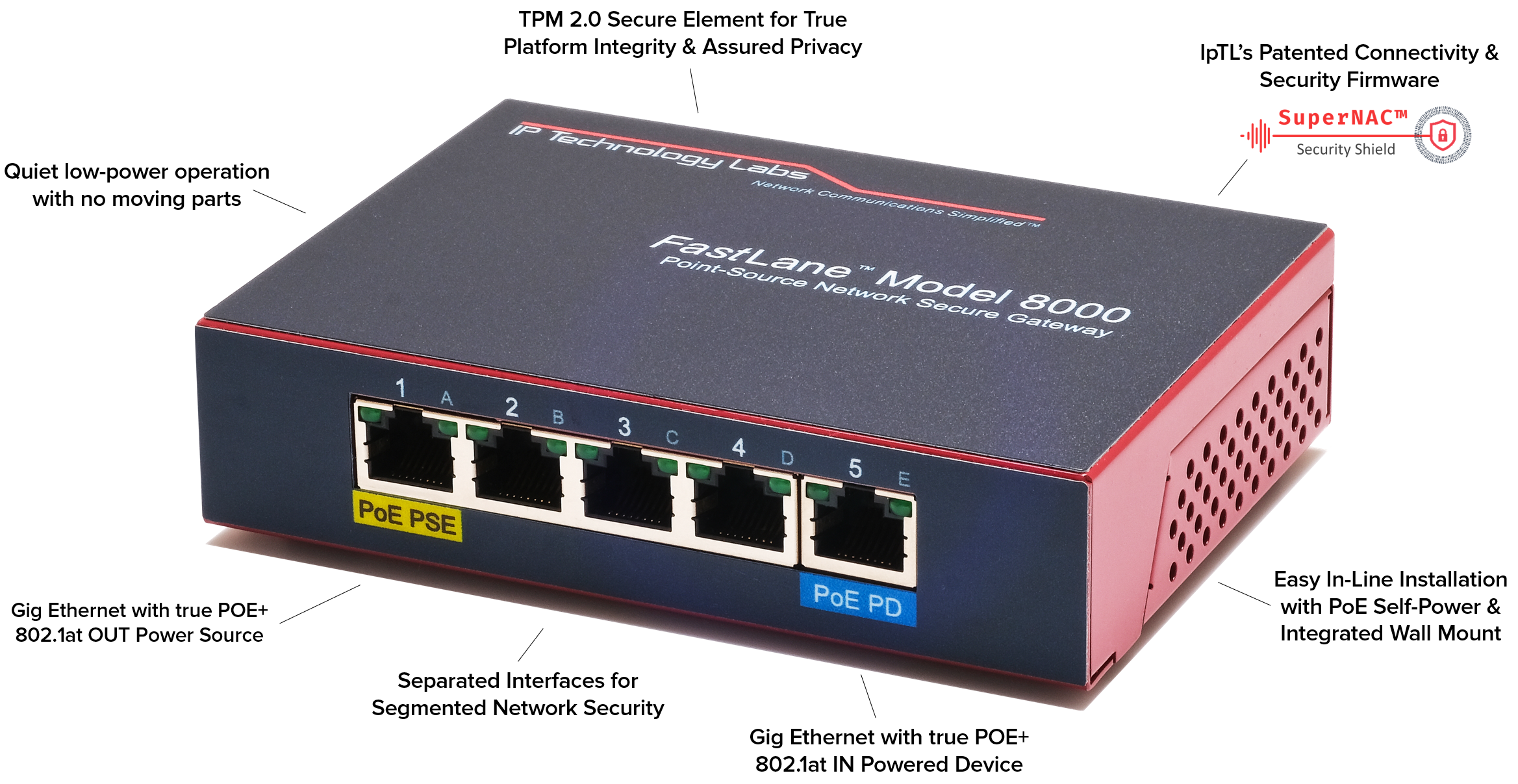
What you should know
- Expandable to 10+ remote connections
- All GiG-Ethernet ports with 10/100/Auto MDI-X
- Hacker Hardened Secure Element with integrated hardware TPM 2.0
- Key vault for Secure Boot, Secure Password, Key & Cert Storage, True Random Number Generator
- 802.1at PoE+ power in (PD Type2/Class4) – powers the appliance
- 802.1at PoE+ power out (PSE Type2/Class4) – powers your PoE device
- Fully Remote out-of-band manageable
- No Fans or moving parts
- Integrated Wall Mount plate & Kensington Lock port
- 5-Port GiG Ethernet Available
- Compatible with all IpTL remote and server appliances
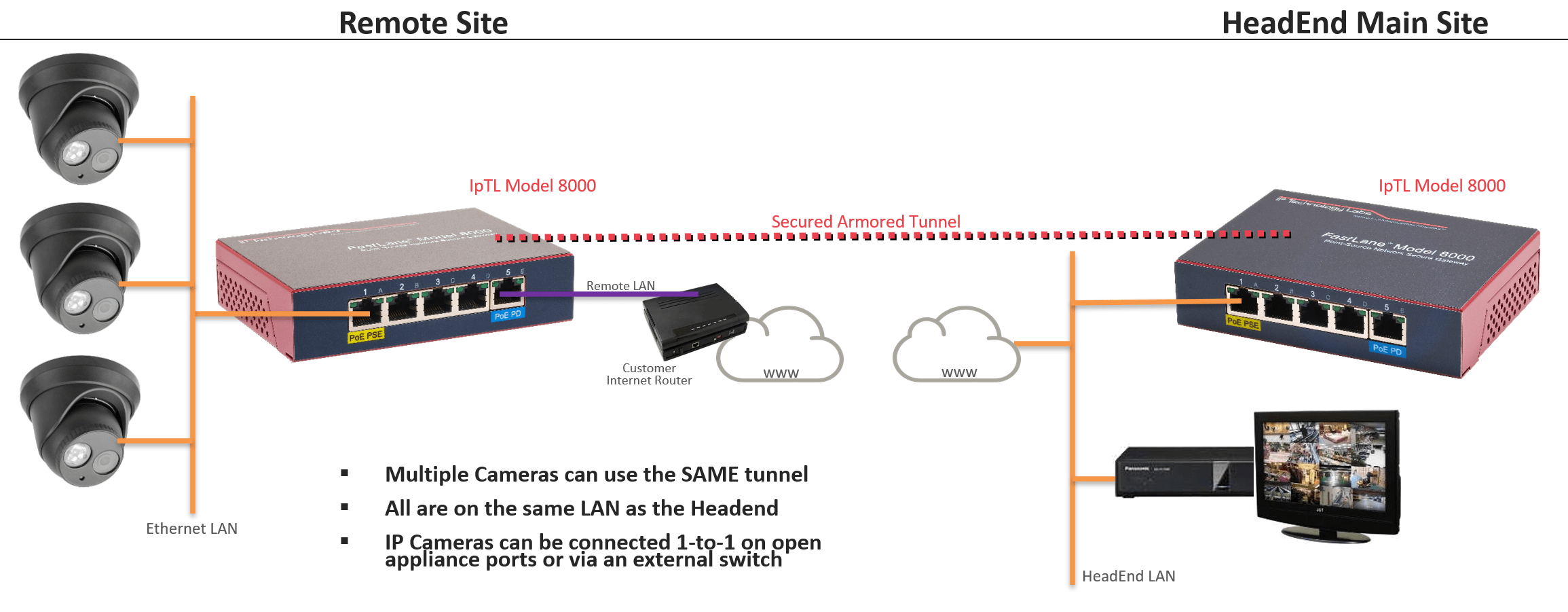
IP Camera to NVR Connectivity
When you have remote IP cameras and NVRs bringing them back to your central site is easy. Using IpTL appliances, you can create highly secure and reliable tunnels over any Internet access…including Dynamic IP and behind firewalls.
You’ll get seamless access without issues of NAT traversal issues. For additional security, use our exclusive SuperNAC conditional network access control to ensure only your camera has access to your headend.
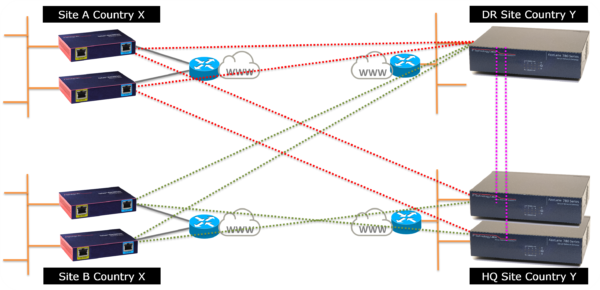
MutiHomed Site-2-Site Full Mesh IoT VPN
IpTL can deliver reliable connectivity and eliminate any single point of failure anywhere in the network. With IpTL, you can interconnect your remote site to multiple head-end locations supporting both headquarters and disaster recovery sites at the same time.
Combined with our SystemMonitor™ dynamic path switching algorithms, we ensure the secure access to your fielded devices regardless of which physical site you are at. Whether you need to protect one circuit or eliminate any single-point-of-failure, IpTL can make your access reliable.
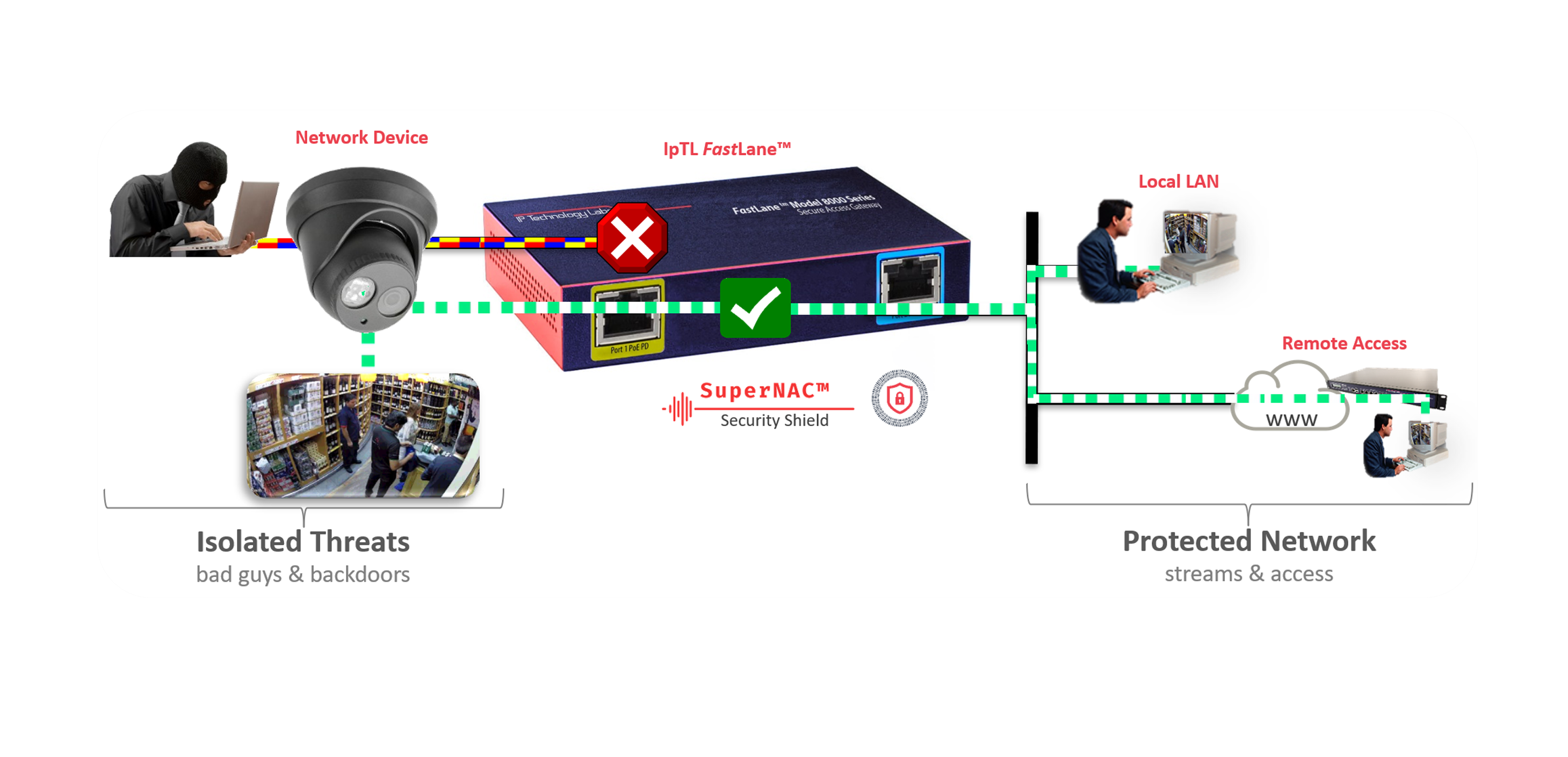
IP Camera/Device Zero Trust Microsegmentation
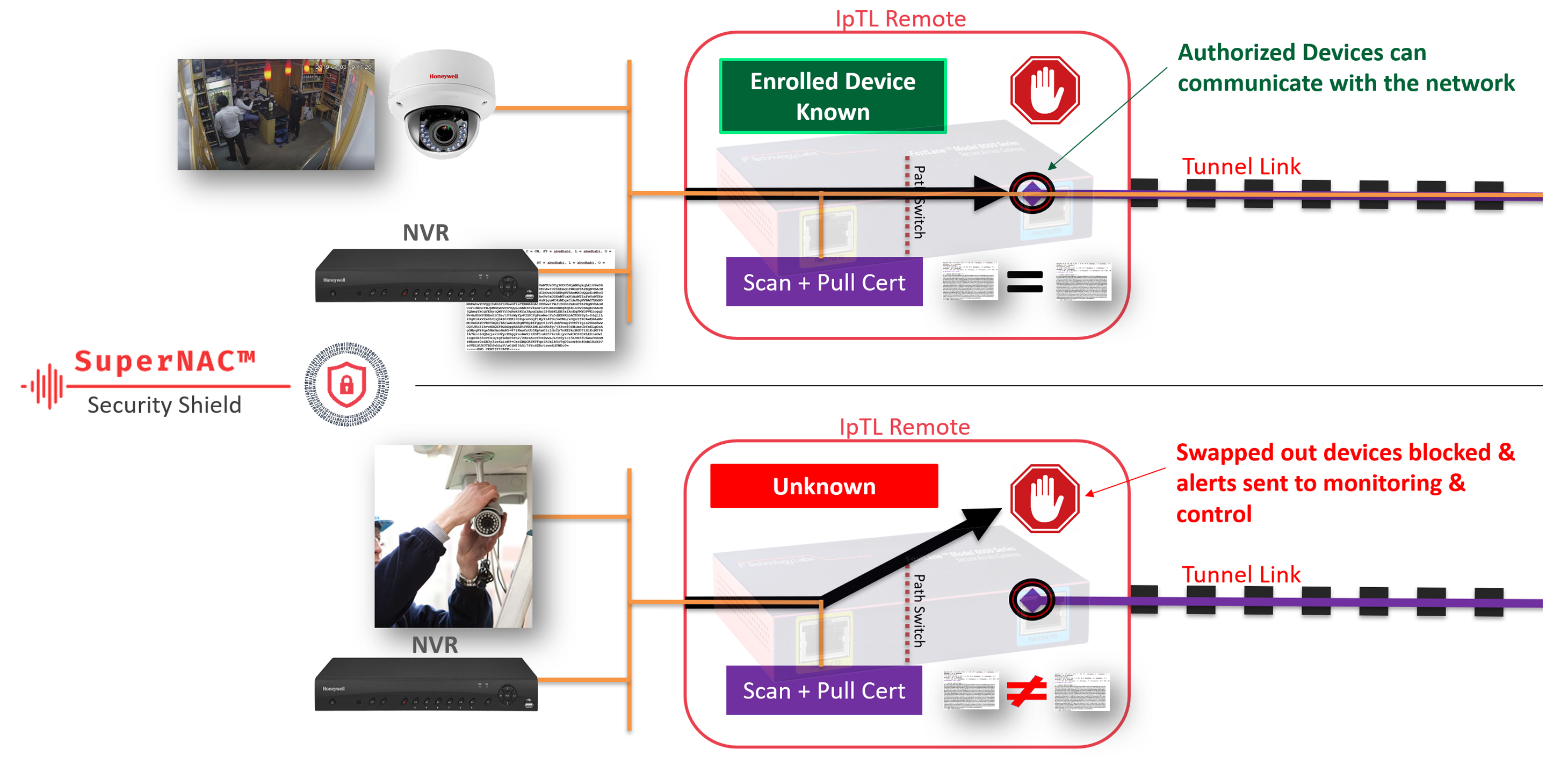
SuperNAC™ can provide agentless identity attribution and provide dynamic data switching. Going beyond just packet headers or MAC addresses, it provides positive assurance that the device you are talking to hasn’t been swapped out. Using active and passive profiling technologies, SuperNAC™ can model the posture of any network device.
IpTL’s patent-pending TrustACL-CERT™ can verify a device’s X.509 cert as well as use built-in v3 cert extensions to control dynamic switching, ACLs, and segmentation for precision control on how and where communications can occur.
SuperNAC™ can also verify a cert through a public Cert Authority or locally with its own built-in authority enabling the use of self-signed certs for true absolute security. For ultimate security, multiple identity methods can be “stacked” to lock-down your important network devices.