SuperNAC™ IoT Network Access Control
Protecting Local Devices & Remote Network Infrastructure from Snooping, Spoofing, and Tampering
SuperNAC™ extends, protects, and automates the protection of local and remote control of IP Cameras, Access Control, and O/T devices. With agentless zero-trust conditional access control features, SuperNAC™ actively protects your network, data, and assures the identity of your IoT devices.
IpTL’s armored remote access tunneling technologies and SuperNAC™ provides the most cost-effective agentless zero-trust network access control to share your remote IoT/M2M devices & applications over any network.
IP Cameras, Access Control, Alarm Panels, & O/T are Vulnerable
SuperNAC™ answers the two most important questions when networking your fixed-application devices and Operation Technology.
- How do I prevent unauthorized access to my device and headend network?
- How do I know the device I’m communicating with is really the device I think it is?
SuperNAC™ features run on your IpTL appliance and put you in control of your IoT device, not on some perimeter firewall.
Most NAC solutions expect you to install a client or run 802.1x. However, fixed application devices such as IP Cameras, and NVRs, Badge Readers are closed systems, and you cannot install a client. SuperNAC™ is agentless, runs on the local appliance, and means no installing, configuring, and paying for a per-host client.
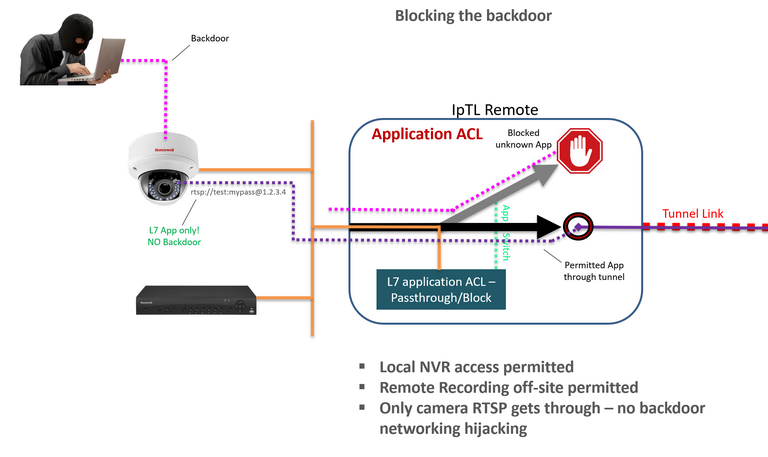
Blocking the Troll.
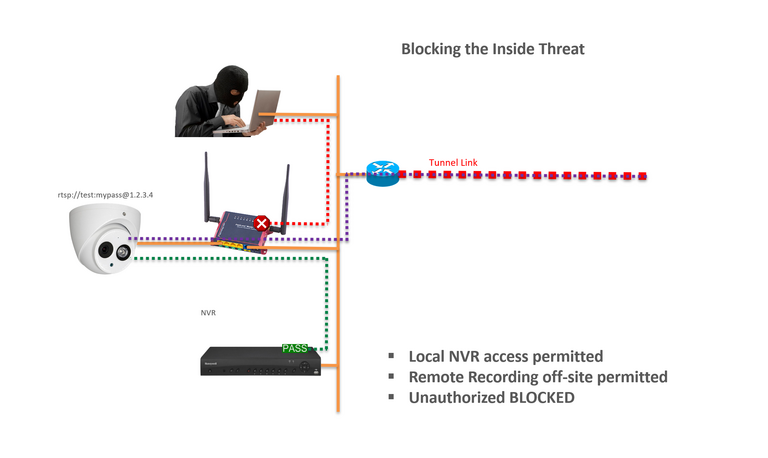
Keeping bad guys out of your devices is tough and even more so when they are inside your network. SuperNAC™ protects your devices, and the integrity of your data, by only enabling access by your authorized devices.
Taking it one step further, even if a device is compromised, the upstream network is protected as only the authorized application stream is available.
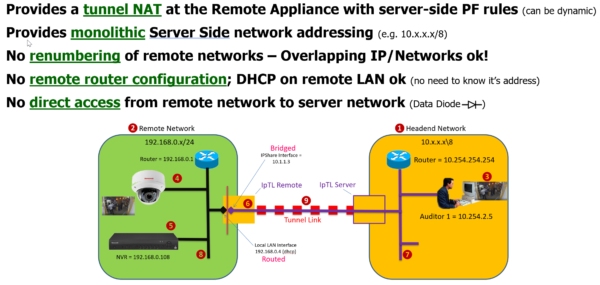
Secure Remote Access without Network Modification
Today’s physical security devices are dual-use and need both local and remote access simultaneously. With IpTL’s SuperNAC™ IPShare™ features, you can get both without network modification and protection from upstream threats.
The ultimate in segmentation, the network is opened only to selective devices and only for the duration of the connection. With IPShare™ the remote network is virtualized and when layered with other SuperNAC™ features like TrustACL-Cert™ and TrustACL-DAA™ you can authenticate both the device and the user.
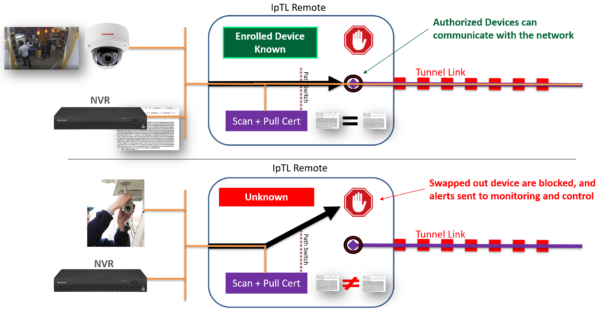
SuperNAC™ can provide agentless identity attribution and provide dynamic data switching. Going beyond looking at just packet headers or MAC addresses, it provides positive assurance that the device you are talking to hasn’t been swapped out. Using active and passive profiling technologies, SuperNAC™ can model the posture of any network device.
IpTL’s patent-pending TrustACL-CERT™ can verify a device’s X.509 cert as well as use built-in v3 cert extensions to control dynamic switching, ACLs, and segmentation for precision control on how and where communications can occur.
SuperNAC™ can also verify a cert through a public Cert Authority or locally with its own built-in authority enabling the use of self-signed certs for true absolute security. For ultimate security, multiple identity methods can be “stacked” to lock-down your important network devices.
The end-point is the perimeter. Microsegment & Zero-Trust.
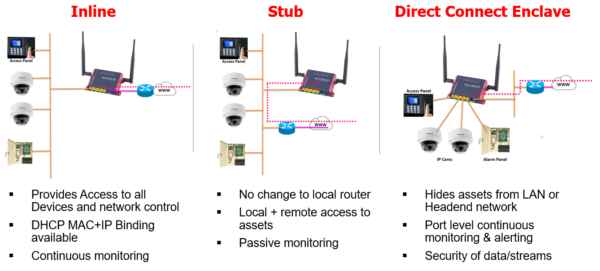
IpTL appliances are flexible. Inline deployment provides base network access and protection. Stub allows local and remote access. Direct Connect Enclave gives the individual port-based segmentation.
With SuperNAC™, you can deploy Connectivity, Trust, and Control in any network deployment.